|
CYBER SECURITY - CLOUD IoT
Please use our A-Z INDEX to navigate this site or return HOME
|
|
PlanetSolar heading out into uncharted technical waters. The theory was in place, but nobody knew if this solar powered boat could make it. But they did! The solar panel area on this ship was increased with solar panels on rollers, pulled out by the crew using winches. The Elizabeth Swann uses robotics and hydraulics to move solar wings that automatically track the sun, and fold away in storm conditions.
WP5. SATELLITE CYBER SECURITY, CLOUD, IoT
Incorporation of (satellite) low-latency encryption and anti-hacking software to prevent:
1. Hijacking of the autonomous asset 2. Ransomeware (malware) 3. Data acquisition 4. Identification and the digital identities of such attempts 5. Repeat offending, with automatic reporting to the authorities 6. Offenders stealing and re-selling data, with IP theft based prosecutions 7. Offenders escaping punishment, via advanced tracking and trojan (virus/spike) implants. Using their own methods against the perpetrators. 8. Profiting from proceeds of crime, via confiscation of black market crypto-currency
This WP can continue to be developed after launch of the vessel, provided that the hardware architecture is designed for independence at the outset.
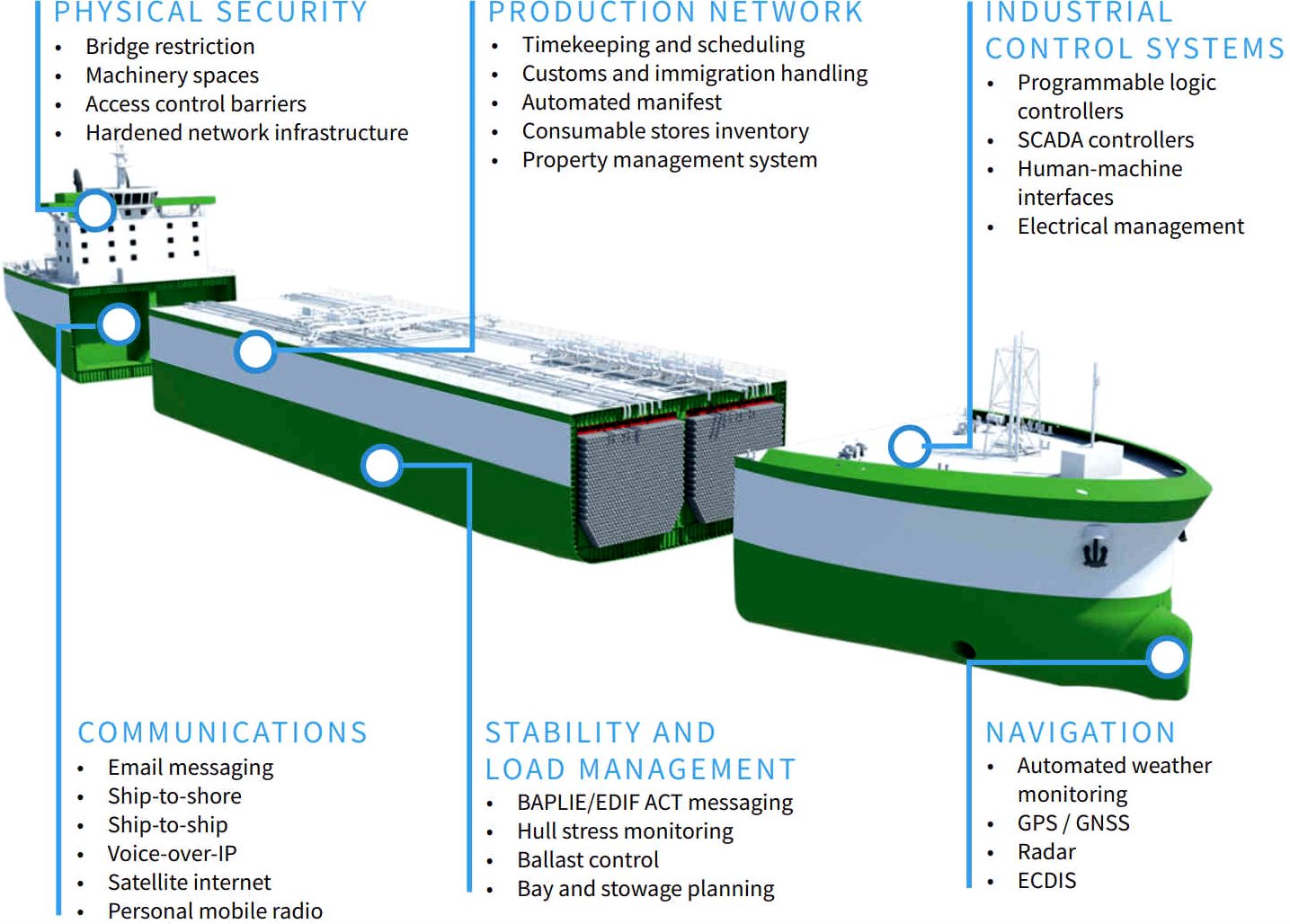
Ship operating systems need to be physically separate from satellite communications, encrypted or not - with reboot flushing on command of an operator, or mechanically, at regular intervals. A software based firewall is not sufficient protection. Difficulties arise mainly from digital communications.
Ports need their own AIS (LRIT) protections. Threat modelling real-world scenarios include:
• Nation states jamming GPS signals to avoid detection of banned trade
• Pirates performing reconnaissance to
determine if the cargo on a ship is what
• Drug cartels moving products through
ports undetected, untargeted malware
LLOYDS
- "It is not only shipping assets which are at risk; the entire shipping sector is
fundamentally dependent upon the same systems which interact with vessels either
for scheduling, loading of cargo, or personnel assignment. Oil extraction
platforms, cargo and loading docks, harbour masters and port authorities all
rely upon the same ageing technical
COVID 19 WAKEUP CALL
The Building Blocks for a Cyber Resilient future has been highlighted because of Covid 19. There is no more business as usual.
Rapid and dramatic changes concerning how and where personnel perform their daily responsibilities require companies to provide that their security infrastructure, controls, processes, and plans are updated and operational.
We have gone through a digital transformation in 2020, that probably would have taken us many
years to realise in ordinary circumstances:
Web applications are the most frequently attacked assets in an IT environment. They present some of the greatest security challenges and are responsible for some of the biggest and most costly attacks.
Prevention strategies focused on network firewalls and user access controls are important,
but they are not sufficient:
-
Understand the requirements to detect attacks at the endpoint, network, cloud, and
A multi-layered security approach could accelerate the transition to the cloud and SaaS with increased agility. This WP is to look at ways of protecting and providing support for zero emission, solar and wind powered vessels.
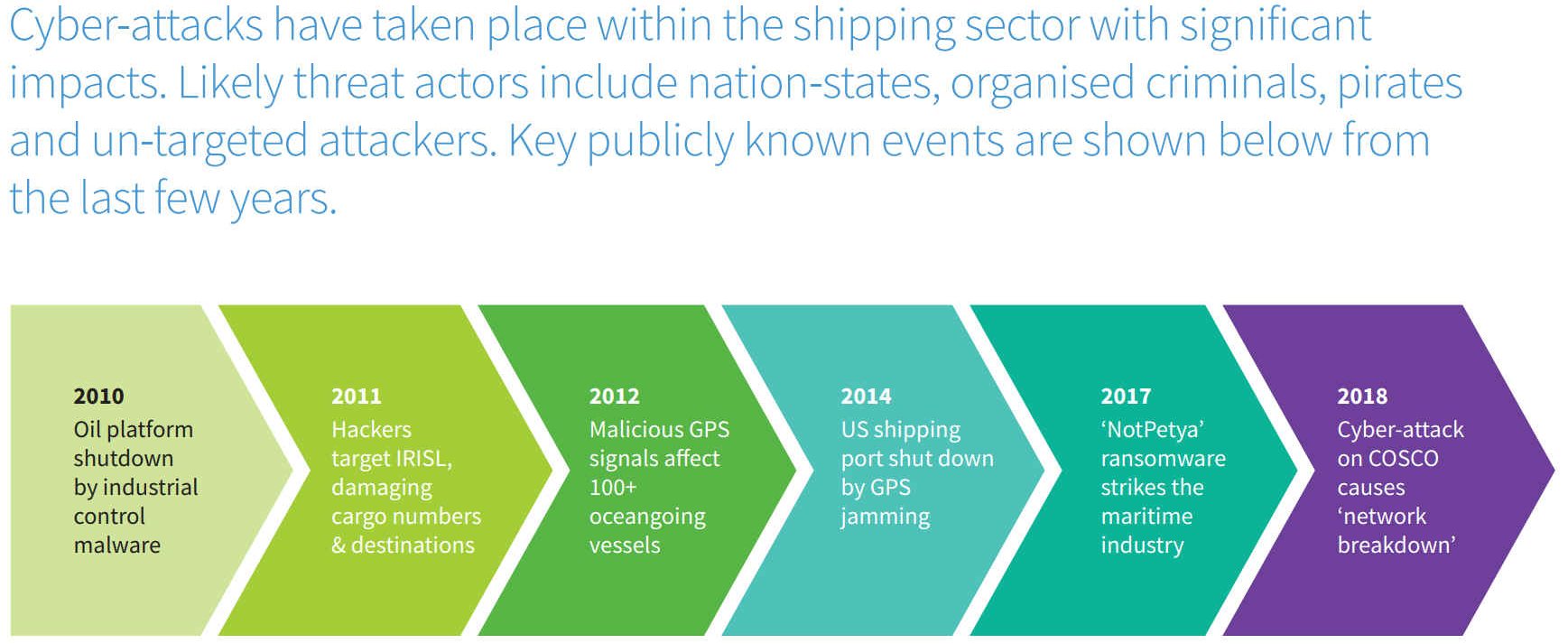
Ransomware is a form of ‘malware’, maliciously created computer software designed to stealthily infiltrate PCs, mobile devices, and even industrial control systems. The variant known as NotPetya represented a particularly aggressive and damaging strain of ransomware, utilizing highly advanced infiltration and lateral movement techniques to infect systems and gain persistence in a target’s network once that access is established.
Once the malicious programme has control of the device, it locks-down access to the device and its functionality before demanding payment in the form of crypto-currency, untraceable digital currency upon which the black-market economy now runs. Clearly, the target must be breaking the crypto currencies and those who provide such services.
MAERSK AS A SHIPPING EXAMPLE - NOTPETYA
A
virus infection can have a significant impact on the shipping sector, reliant as it is upon
interconnectivity and reliable, accurate information exchange.
The estimated financial impact was:
•
USD $200,000,000 million dollars
Even if not directly targeted themselves, shipping company assets can rapidly fall
WP3. PLATFORM BUILD WP4. GIS, GEOSPATIAL AI INCORPORATION WP5.
SATELLITE CYBER SECURITY, CLOUD, IoT
WP11. ONBOARD/OFFBOARD VESSEL SECURITY WP12. AUTONOMOUS CIRCUMNAVIGATION ATTEMPT WP13. COLREGS COMPLIANCE LAW & LOBBYING
The Cleaner Ocean Foundation works to help protect the "seven seas" from the effects of anthropogenic atmospheric pollution like this ship that is belching diesel fumes like there is no tomorrow. We'd like to preserve tomorrow for our children. You can help us to make this scene a thing of the past.
WHY ARE WE DOING THIS?
Because we can, and because we can, we must.
|
|
|
Please use our A-Z INDEX to navigate this site
This website is Copyright © 2020 Jameson Hunter Ltd
|